In This Post, I created certificates for my SRM & vCenter servers where I used a separate signing authority. What if you don’t have one, but still want to use your own certs? You create your own Root Certificate Authority (root CA) via OpenSSL. Here’s how…
Creating Certificates for VMware SRM or vCenter using openSSL made easy, with Video!
Some of the documentation around creating certificates for vCenter or SRM seems to be lacking, so I documented a few steps for each and outlined the differences, also created a video :)
This can be done from any machine, as long as openssl is installed. If you’re creating/requesting multiple certs, create folders for each request and work from within there so you don’t mix them up. I use d:\cert\vcenter and d:\cert\srm. I added “D:\OpenSSL-Win32\bin\” to may path variable so it’ll work in any folder I’m in.
How to determine RAM speeds on Dell’s new 12G servers with Intel Sandy Bridge Xeon E5-2600 Procs
I’m sure many of you have dealt with trying to figure out how much RAM you can shove in a box, say an R720, and still keep RAM speeds up. I actually had some docs from Dell, figures, diagrams, graphs, and a few charts. Even then, it was difficult.
Enter the “Dell 12G Memory Solution Tool”. It is a website that allows you to test RAM & CPU configurations to get optimal speeds. For instance, you can select the R720, 2 CPUs, and that you want 256GB of RAM. That’s a nicely sized box for virtualization. The tool tells me I can get 16x 16GB of 2R4 DIMMS at 1333MHz or 1600MHz. Of course, I’m going to go with the 1600MHz! What if I want to bump the RAM? I checked out 384GB & 512GB to see how they stack up; 384GB gives me the option for 24 16GB DIMMS, but drops my speed to 1066; and 512GB has two options, either 800MHz, or 1333MHz (yes please!).
It also shows you some quick price & power consumption rankings on a 1-5 scale.
Pretty awesome, imo! Here’s the link: http://poweredgecpumemory.com/
Next release of #PowerCLI will stop on invalid certificates
I’m a little late to the game, but finally got around to installing PowerCLI 5.0.1. Upon connecting to my lab vCenter, I learned of the behavior change that will appear in future releases of PowerCLI. In short, you won’t be able to connect.
By default, it’s unset: ![]()
To change that, set the Invalid Certificate Action to Ignore: ![]()
You simply type this:
|
1 |
set-PowerCLIConfiguration -invalidCertificateAction "ignore" -confirm:$false |
It could potentially break all your scripts if you upgrade to whatever’s after 5.0.1.
Function to convert VMs from thin to thick using #PowerCLI & #PowerShell
Most people want to go from thick to thin to save space. I, on the other hand, want to convert my VMs from thin to thick. Thin provisioning buys you time, basically, but what do you do when you’re vastly over provisioned and your VMs are filling up available physical storage? Sure, you can manually go to each VM and use the GUI to migrate them and convert each one to thick. I had a couple hundred that were thin provisioned and needed them converted to thick.
I’ve been moving from 500GB LUNs to 1TB LUNs, so I scripted it out to migrate VMs over, as well as convert to thick using the New-Object cmdlet.
Easy way to check if your PowerShell variable is an array or not
I had a script that assumes something was an array, then failed when it wasn’t, so I needed a little checking:
$variable -is [system.array] will say True if it is an array, or False if not. You can also do $variable -isnot [system.array] and expect the exact opposite.
I chose to do this:
|
1 |
if($variable -isnot [system.array]){do some code expecting the $variable is not an array} |
OR
|
1 |
if($variable -is [system.array]){do some other stuff with $variable[0] being an array} |
Use Powershell to change SCCM cache directory & cache size
Some of our older servers are running out of disk space on C:, so I needed to change the SCCM cache directory to D:. By default, this is where I wanted it anyway on our servers, leaving C: only for OS-related files. My OSD Task Sequences all have SMSCACHEDIR set to a folder on D in the client configuration step, but I noticed it wasn’t actually working. You know I had to find a way to fix that using powershell :D It actually ended up being really REALLY easy to do…
VMware VirtualCenter Management Webservices fails to start with error code 0
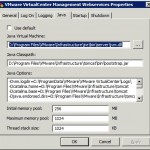
I did an in-place upgrade of vCenter to 5.0 from 4.1 and everything seemed to go fine. When I checked heartbeat, it was barking about some services, so I checked and sure enough, VMware VirtualCenter Management Webservices wouldn’t start.
I checked the commons-daemon log file (located here Program Files\VMware\Infrastructure\tomcat\logs) and found this:
[2012-03-01 08:32:36] [info] Commons Daemon procrun (1.0.5.0 64-bit) started
[2012-03-01 08:32:36] [info] Running ‘vctomcat’ Service…
[2012-03-01 08:32:36] [info] Starting service…
[2012-03-01 08:32:37] [error] Failed creating java
[2012-03-01 08:32:37] [error] ServiceStart returned 1
[2012-03-01 08:32:37] [info] Run service finished.
[2012-03-01 08:32:37] [info] Commons Daemon procrun finished
I did some googling, which had suggestions such as lowering the VM heap size from 1024MB to 512MB, checking for port conflicts, etc. What fixed it for me was specifying the location of jvm.dll in the jre that came with the vCenter installation. It’s highlighted in the attached pic, which I installed on D, yours may be different. After that, vctomcat started fine.
NetApp SnapMirror & RDMs – Automated failover
A few months ago, a reader by the name of Tolga ŞENTEKİN came across This Post looking for something to do a little more. Tolga was looking to script out DR for some VMs he has that use NetApp with & without RDMs. He & I spent about three weeks putting a script together to do the following:
- Breaks snapmirror replication
- Creates flexclones of the replicated volumes (given you’re licensed for it)
- Map them to the esx hosts on the disaster recovery site
- Adds and resignatures the LUNs and adds the VMs inside them to the inventory
- After that, if you have RDM LUNs attached to the VMs, you first remove the old RDM Mappings from the VM and add the actual LUNs in the disaster site with the same LunID’s
- If it’s all done you can start the Vm’s in the disaster site.
Tolga wrote the vast majority of the script, with me only contributing some of the datastore, LUN, & iSCSI stuff.
I uploaded it and have provided a link, since I didn’t want it to get sauteed up from a C&P.
Click HERE to download a copy of the script (right-click, save-as). Obviously, you will need to edit & fine tune for your environment, but he & I wanted to share with the community.