TL-DR: See below for details on these commands
Create a local user in the NSX Manager’s CLI, then use the API to grant CLI privileges to that user.
Here’s how using a linux machine:
ssh admin@[nsxmanagerIP]
enable
config t
user vrops-readonly password plaintext notrealpassword
user vrops-readonly privilege web-interface
Log out of the NSX Manager (type exit) and stay logged into the linux machine.
Create cli-auditor.xml that contains this (replace brackets with greater/less than):
[?xml version="1.0" encoding="ISO-8859-1" ?]
[accessControlEntry]
[role]auditor[/role]
[resource]
[resourceId]globalroot-0[/resourceId]
[/resource]
[/accessControlEntry]
Add the user as an auditor in the NSX Manager as a CLI user:
curl -i -k -u 'admin:password' -H "Content-Type: application/xml" -X POST --data "@cli-auditor.xml" https://nsxmanagerip/api/2.0/services/usermgmt/role/vrops-readonly?isCli=true
Add your domain/vCenter user as an auditor in the NSX Manager (NOT as a CLI user):
curl -i -k -u 'admin:password' -H "Content-Type: application/xml" -X POST --data "@cli-auditor.xml" https://nsxmanagerip/api/2.0/services/usermgmt/role/[email protected]?isCli=false
Details for creating the NSX CLI user for vROps
Last week, Jonathan Somers (@vdudejon) set up probably the largest VMware vRealize Operations cluster consisting of 16 nodes and a bunch of remote collectors, with over 63k VMs, nearly 10k hosts, for a total of 107K objects & nearly 25 MILLION METRICS! Since I deployed NSX for the Distributed Firewall in our environment, we thought it’d be cool to tack on the NSX Management Pack to see what other info we can get.
Installing the plugin itself into vROps was simply:
- Download PAK file
- Log in to vROps, go to Administration, Solutions, Add
- Upload PAK file
- Finish
That’s no big deal, super simple, anyone can do that. Configuring the management pack, that’s a little different. Once in the Solutions section, you should see “Management Pack for NSX-vSphere”, select it and click the Configure icon.
That’s where you’re prompted with this:
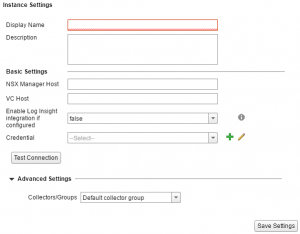
Again, simple, until you get to the credentials portion. Inside there you’ll notice there are two credentials needed; NSX Manager, & vCenter:
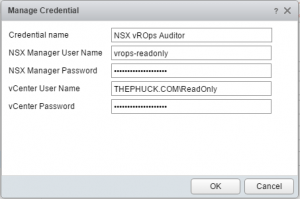
I tried using the same domain credentials for both, which it failed to talk to the NSX Manager. I tried with the NSX Manager admin account, and that worked. Now, not wanting to give elevated privileges, I wanted to create a read-only account for the NSX Manager, aka “Auditor” account. I also wanted to make sure the vCenter account was also an Auditor, which already existed in vCenter with Read-Only permissions.
I started doing some research and came across this post, which outlines how to create NSX Manager local users to access the API & add them as CLI users. I stepped through this and tested each step, hoping to find the minimal amount of privileges needed for the account. Alas, I did have to create the user, grant “web-interface” privileges, and add as a CLI user.
I tried hitting the REST API using PowerShell (invoke-restmethod), but I was bitten by the pesky self-signed cert problem that I couldn’t ignore, so I decided to hop onto a linux box and use curl. That worked flawlessly!
Here’s how:
First thing’s first, you need to create the user in the NSX Manager. SSH into the NSX Manager, enable, then config t, and run the following:
|
1 |
user vrops-readonly password plaintext notrealpassword |
That simply creates the “vrops-readonly” user, change “notrealpassword” to a password of your choosing, now we need to grant the web-interface privilege
|
1 |
user vrops-readonly privilege web-interface |
We’re done with the NSX Manager, you can log out of it, now the fun part. The ONLY way to grant CLI privileges (or at least the only way I found via the above link) was via the API. DO NOT add the user as an Auditor in the WebClient, the API will error out stating the user already exists. I suggest you use a linux machine for this, as it’s very simple. You’ll need to create an xml file to serve as the body of the POST command:
[?xml version="1.0" encoding="ISO-8859-1" ?]
[accessControlEntry]
[role]auditor[/role]
[resource]
[resourceId]globalroot-0[/resourceId]
[/resource]
[/accessControlEntry]
Use youre favorite text editor to create the .xml file (I named it “cli-auditor.xml”, change the [ and ] to greater than & less than as needed (I couldn’t use those here, the tags disappeared). As you can see, the role granted is Auditor, and it’s assigned to the global root.
Now, we need to do a POST with the API to enable the CLI privilege:
|
1 |
curl -i -k -u 'admin:password' -H "Content-Type: application/xml" -X POST --data "@cli-auditor.xml" https://nsxmanagerip/api/2.0/services/usermgmt/role/vrops-readonly?isCli=true |
If it worked correctly, you should get an HTTP 204 No Content status. That uses a simple cURL command & ignores the certificate, then does a POST of the XML file to user and sets “isCli” as true, thus granting CLI privileges.
Now, if you do a curl GET on that user:
|
1 |
curl -i -k -u 'admin:password' -X GET https://nsxmanagerip/api/2.0/services/usermgmt/user/vrops-readonly |
You’ll see a bunch of xml, and one that specifically says [isCli]true[/isCli].
That’s created the user on your local NSX Manager, as well as granted API/CLI access & Auditor privileges, but what if you still needed to add your domain read-only vCenter user as an Auditor in the NSX Manager? Simple! Run the same command targeted at the domain user. However, you’ll want to set “isCli=false” so it’s not added to the NSX Manager as a CLI user, too (no elevation of privileges :)):
|
1 |
curl -i -k -u 'admin:password' -H "Content-Type: application/xml" -X POST --data "@cli-auditor.xml" https://nsxmanagerip/api/2.0/services/usermgmt/role/[email protected]?isCli=false |
Now, when configuring the NSX Managers in vROps, save the credentials as something like “NSX Auditor” so you can reuse them if you have more than one NSX Manager to add. The last step is simply providing the vCenter, the NSX Manager, selecting your newly created credentials, and saving the config. Of course, you’ll have to tell it to ignore/accept the certificate if it’s still self-signed, and then you’ll be collecting data:
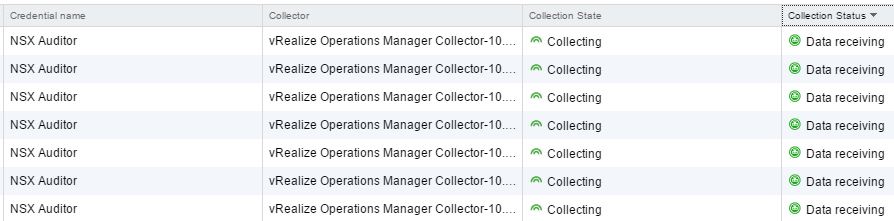
After that, I was able to add the NSX Managers into the massive vROps cluster and begin collecting data.
Creating a Security Administrator API user?
I also wanted to point out this same process to create the local user on the NSX Manager is how you’d create API users for NSX. They’re local accounts who have access to the API, so if you’re a programmer and consuming the API, this is the route to go, and not using the Admin user account. Using the API to add the new account as a CLI user outlined above, you’d want to change “auditor” to “security_admin” to allow you to make changes in NSX, not just a read-only account.
Hope this helps anyone as lost as I was!