In This Post, I created certificates for my SRM & vCenter servers where I used a separate signing authority. What if you don’t have one, but still want to use your own certs? You create your own Root Certificate Authority (root CA) via OpenSSL. Here’s how…
You need to download and install OpenSSL from Here. I installed mine on the D drive, D:\OpenSSL-Win32, then added “D:\openssl-win32\bin” to my path. There are some prereqs needed:
- You’ll need an openssl.cnf file in that directory
- Folder structure for Root CA
- Serials for certs
- I think that’s it
First thing’s first, the openssl.cnf file: openssl.cnf. Most of these files you find on the web have the demoCA folder, so I left it and just changed the path to that. I also added the v3_ca extension at the bottom.
Next is the folder structure, you need to create the ‘demoCA’ directory under the bin folder, and a ‘newcerts’ folder under that:mkdir d:\openssl-win32\bin\demoCA\newcertsThat creates both for us.
Now we need to copy the serial file over, for certificate serial numbers:copy d:\openssl-win32\bin\pem\democa\serial d:\openssl-win32\bin\democa
Lastly, we need an empty index.txt file. You can do this however you wish, but an easy way is via notepad & cli:notepad d:\openssl-win32\bin\demoCA\index.txtIt will prompt you that it doesn’t exist and needs to create it. That’s what we want, save and close it once opened.
Now the fun part of actually creating your root CA, simply run this from wherever you want:openssl req -new -x509 -extensions v3_ca -keyout rootca.key -out rootca.crt -days 3653 -config openssl.cnf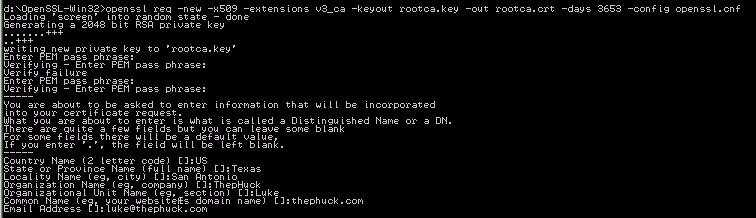
Can you guess why I did 3653? I ran it from the d:\openssl-win32 directory, which is where my openssl.cnf file is located. Now, this command created our rootca.key and rootca.crt files. If you do a dir rootca*, you should see them.
Some things to note:
Enter PEM pass phrase: <--- this should be a $tr0n6 P@s$w0rd that you can keep track of, you'll have to use it when signing certs, same with these:Country Name (2 letter code) []:USWhen creating CSRs, some fields are required to match what the root CA has, some just need not be blank, and others are optional. This is governed by the opennssl.cnf file and needs to be set BEFORE creating the root CA. My supplied openssl.cnf file has the following:
State or Province Name (full name) []:Texas
Locality Name (eg, city) []:San Antonio
Organization Name (eg, company) []:ThepHuck
Organizational Unit Name (eg, section) []:Luke
Common Name (eg, your websiteÆs domain name) []:thephuck.com
Email Address []:[email protected]# For the CA policy
[ policy_match ]
countryName = match
stateOrProvinceName = match
organizationName = supplied
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ policy_anything ]
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
Moving on…we’re going to overlap a little from yesterday’s post regarding Certificate Signing Requests (CSRs), but I’m not going in to detail on that. Let’s say we already have our csr file and need to sign it.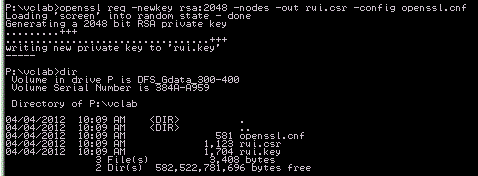
Now we need to sign that csr file. I ran this command from my p:\vclab folder, which requires us to supply the path to rootca.key, rootca.crt, and root CA’s openssl.cnf file:openssl ca -cert d:\OpenSSL-Win32\rootca.crt -keyfile d:\OpenSSL-Win32\rootca.key -out rui.crt -config d:\OpenSSL-Win32\openssl.cnf -infiles rui.csrThis will have a few prompts, like the $tr0n6 P@s$w0rd pass phrase we entered earlier, then it checks the supplied attributes. If you look in my output below, that was for SRM (it contains Extended Key Usage). You have to type Y to sign the cert, then commit it, then you’re done: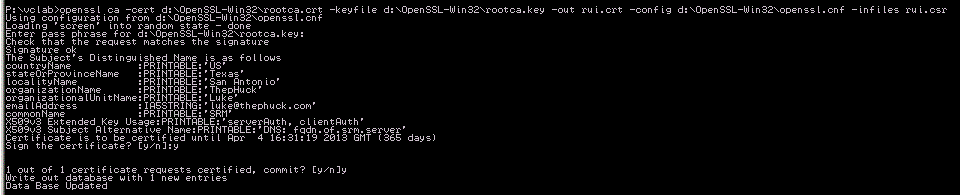
Any additional certificate-related steps for vCenter or SRM are covered in yesterday’s post. If you use this cert we just signed, you’ll still get a warning that it is untrusted. Can you guess why? Yup, dragons around every corner, I know. Your local machine doesn’t trust the certificate authority. You have to import the rootca.crt file into your Trusted Root Certificate Authority. You can also blast that out via GPO.
Awesome…
Short and sweet..
Thanks for the tutorial, my biggest issue is that openSSL fails to run despite Windows SDK and the necessary Visual C++ 2008 Redists being installed.
Next time please mention the necessary requirements to actually get openSSL to run, please.
It’s worth mentioning, but that’s part of getting OpenSSL up and running properly by itself.